A fix for multiple vulnerabilities affecting all uTorrent, BitTorrent and uTorrent Web Windows users is now available for immediate download at the links below. We must stress that while this is a vulnerability that can be exploited to trigger unauthorized downloads to take place, BitTorrent Inc. is not aware of any incidents related to these vulnerabilities. As always, we highly encourage all of our customers to stay up to date. Android and Mac users are not affected by the reported vulnerabilities.
Download the latest builds:
uTorrent Stable 3.5.3.44358
Bittorrent Stable 7.10.3.44359
uTorrent Beta 3.5.3.44352
uTorrent Web 0.12.0.502
The team began rolling out the update to beta uTorrent Windows users via the auto update mechanism on Feb 16, 2018. As of today, Feb 22, 2018, the rollout for beta users has concluded and the stable rollout has started. Included in the latest builds are fixes to the way uTorrent and uTorrent Web authenticate WebUI requests and generate session and authentication tokens. In addition to this, the updates clamp down on guest account access limits and enforce more checks on potentially malicious HTTP headers sent to the client.
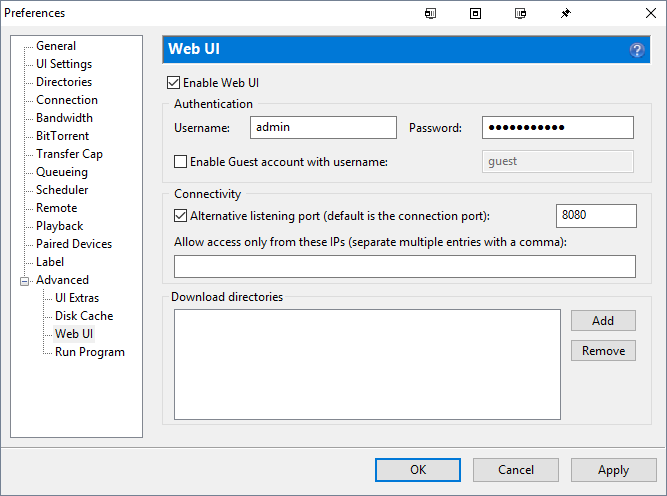
Customers and developers of 3rd-party applications that rely on the default-open state of port 10000 should be aware that moving forward, clients will no longer be discoverable over port 10000. Pairing negotiation is now only allowed over a mutually agreed upon port. Customers can set this port manually by enabling WebUI functionality via Advanced->WebUI-> Enable Web UI and then specifying a port under the Connectivity section.
You can find the full changelog here:
